Ensure that you have set up sphere provider provider, refer my previous blog https://blog.ntitta.in/?p=597
create a windows profile
/etc/salt/cloud.profiles.d/w16k.conf
root@saltyub:/# cat /etc/salt/cloud.profiles.d/w16k.conf
w16k:
provider: vcsa
clonefrom: w16k_salt
# devices:
# network:
# Network adaptor 1:
# name: VM Network
# adapter_type: vmxnet3
# switch_type: standard
# ip: 172.16.70.79
# gateway: [172.16.1.1]
# subnet_mask: 255.255.128.0
# domain: ntitta.lab
cluster: vSAN
datastore: vsanDatastore
power_on: True
deploy: True
customization: True
minion:
master: saltyu.ntitta.lab
win_username: administrator
win_password: 'P@ssw0d'
plain_text: True
win_user_fullname: admin
win_run_once: 'powershell.exe c:\scripts\e.winrm.ps1'
win_installer: /salt/minion/Salt-Minion-3000.9-Py2-AMD64-Setup.exe
winrm_verify_ssl: False
Ensure that you have the smbprotocol and pypsexec installed
pip3 install smbprotocol
pip3 install pypsexec
on the guest windows server template, ensure vmware tools is installed and create a PowerShell script in the path: c:\scripts\e.winrm.ps1, refer salt doc for more information: https://docs.saltproject.io/en/latest/topics/cloud/windows.html
New-NetFirewallRule -Name "SMB445" -DisplayName "SMB445" -Protocol TCP -LocalPort 445
New-NetFirewallRule -Name "WINRM5986" -DisplayName "WINRM5986" -Protocol TCP -LocalPort 5986
winrm quickconfig -q
winrm set winrm/config/winrs '@{MaxMemoryPerShellMB="300"}'
winrm set winrm/config '@{MaxTimeoutms="1800000"}'
winrm set winrm/config/service/auth '@{Basic="true"}'
$SourceStoreScope = 'LocalMachine'
$SourceStorename = 'Remote Desktop'
$SourceStore = New-Object -TypeName System.Security.Cryptography.X509Certificates.X509Store -ArgumentList $SourceStorename, $SourceStoreScope
$SourceStore.Open([System.Security.Cryptography.X509Certificates.OpenFlags]::ReadOnly)
$cert = $SourceStore.Certificates | Where-Object -FilterScript {
$_.subject -like '*'
}
$DestStoreScope = 'LocalMachine'
$DestStoreName = 'My'
$DestStore = New-Object -TypeName System.Security.Cryptography.X509Certificates.X509Store -ArgumentList $DestStoreName, $DestStoreScope
$DestStore.Open([System.Security.Cryptography.X509Certificates.OpenFlags]::ReadWrite)
$DestStore.Add($cert)
$SourceStore.Close()
$DestStore.Close()
winrm create winrm/config/listener?Address=*+Transport=HTTPS `@`{CertificateThumbprint=`"($cert.Thumbprint)`"`}
Restart-Service winrm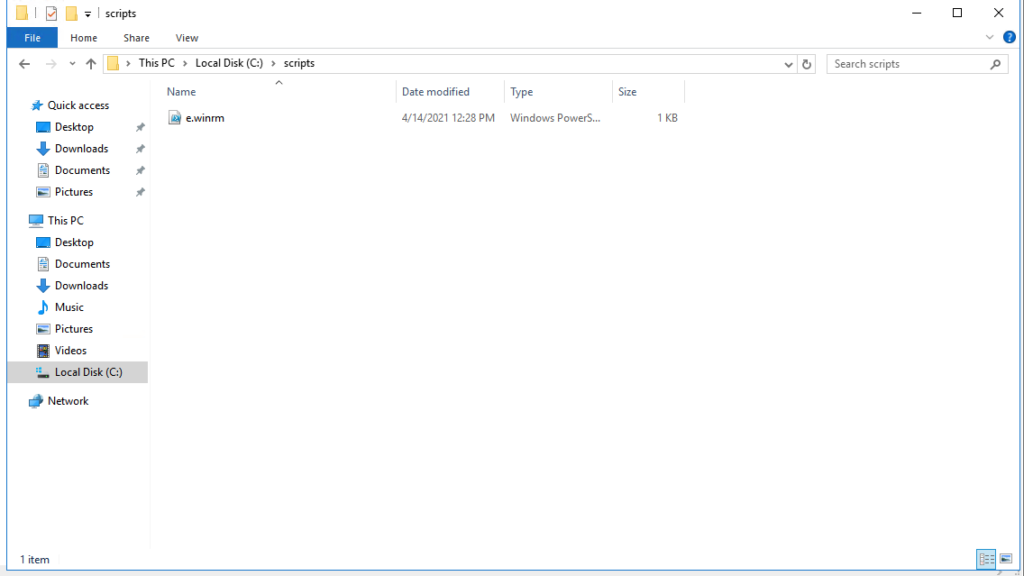
download salt windows minion installer to the below path on the salt-master:
/salt/minion/, exe can be downloaded from https://docs.saltproject.io/en/latest/topics/installation/windows.html
wget https://repo.saltstack.com/windows/Salt-Minion-3003-Py3-AMD64-Setup.exeDeploy Windows VM via salt:
salt-cloud -p w16k w16k-salty-minion -l debugDeployed VM you can see firewall and salt minion installed:
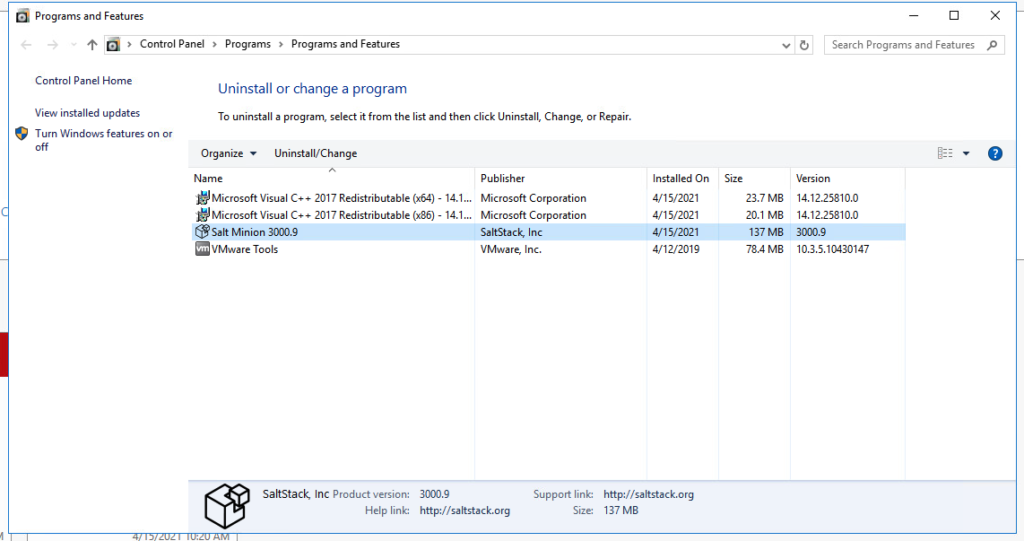
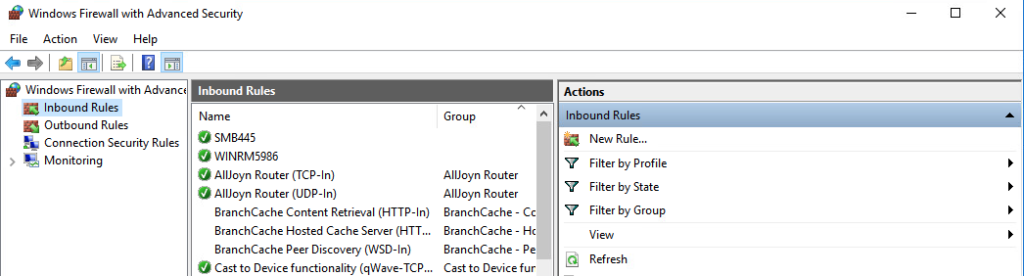
Troubleshooting:
[ERROR ] Unable to execute command
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/salt/utils/cloud.py", line 1005, in wait_for_psexecsvc
stdout, stderr, ret_code = run_psexec_command(
File "/usr/lib/python3/dist-packages/salt/utils/cloud.py", line 956, in run_psexec_command
client = Client(
File "/usr/lib/python3/dist-packages/salt/utils/cloud.py", line 879, in __init__
self._client = PsExecClient(server, username, password, port, encrypt)
NameError: name 'PsExecClient' is not defined
cause: PsExecClient module is not installed. , use pip3 to install this