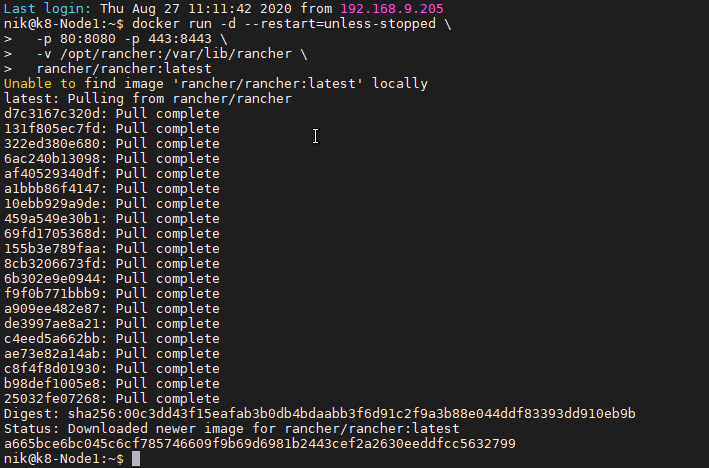
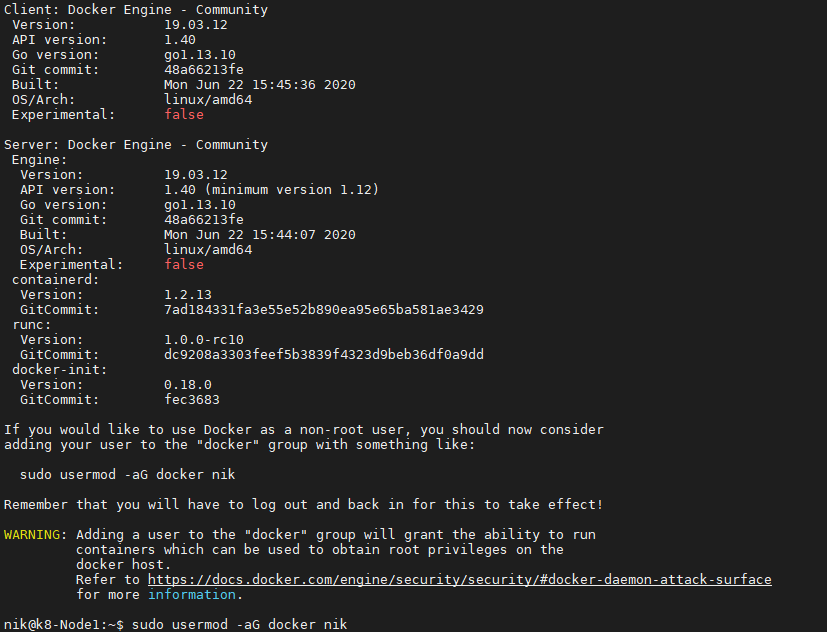
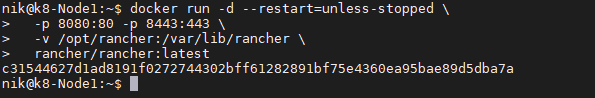
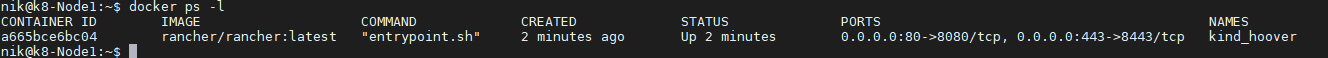
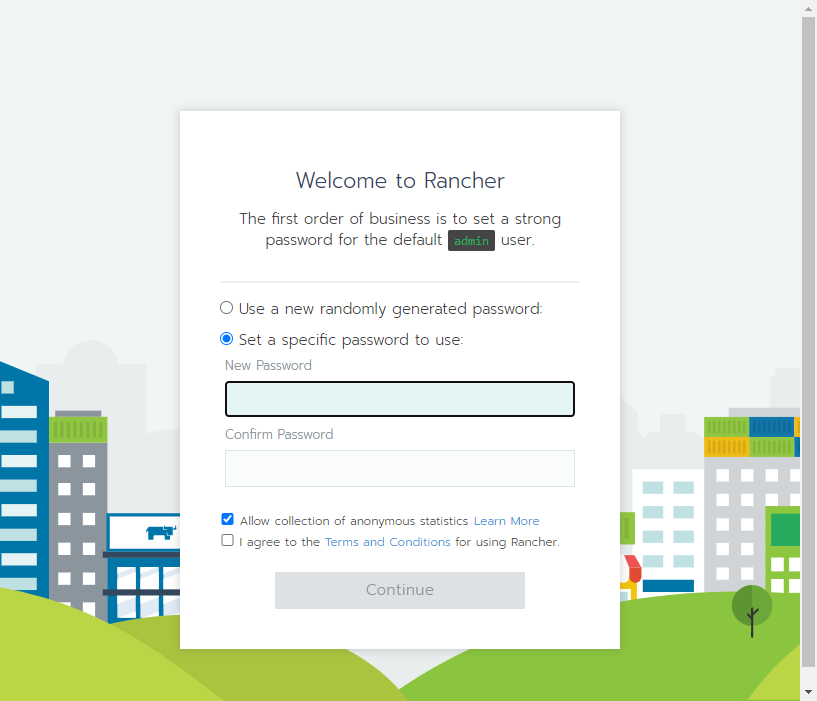
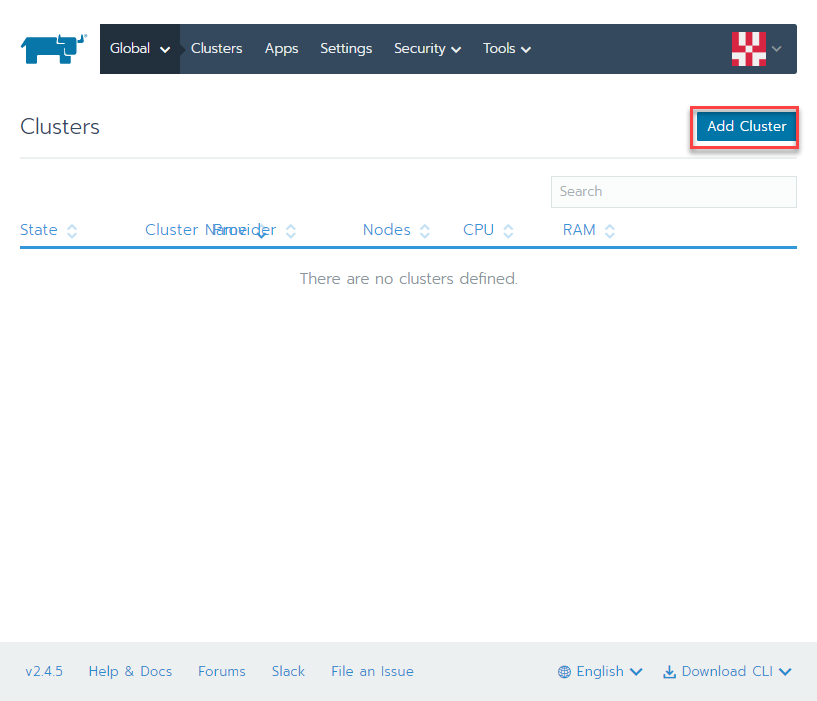
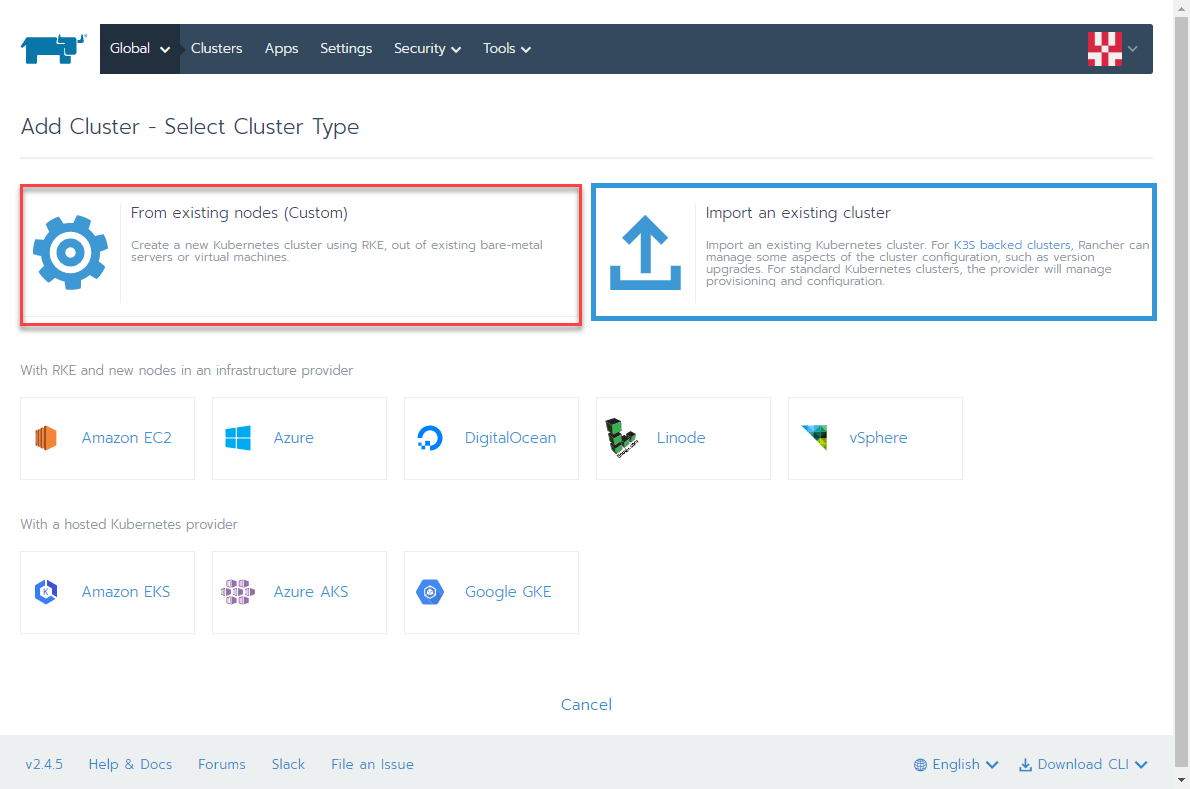
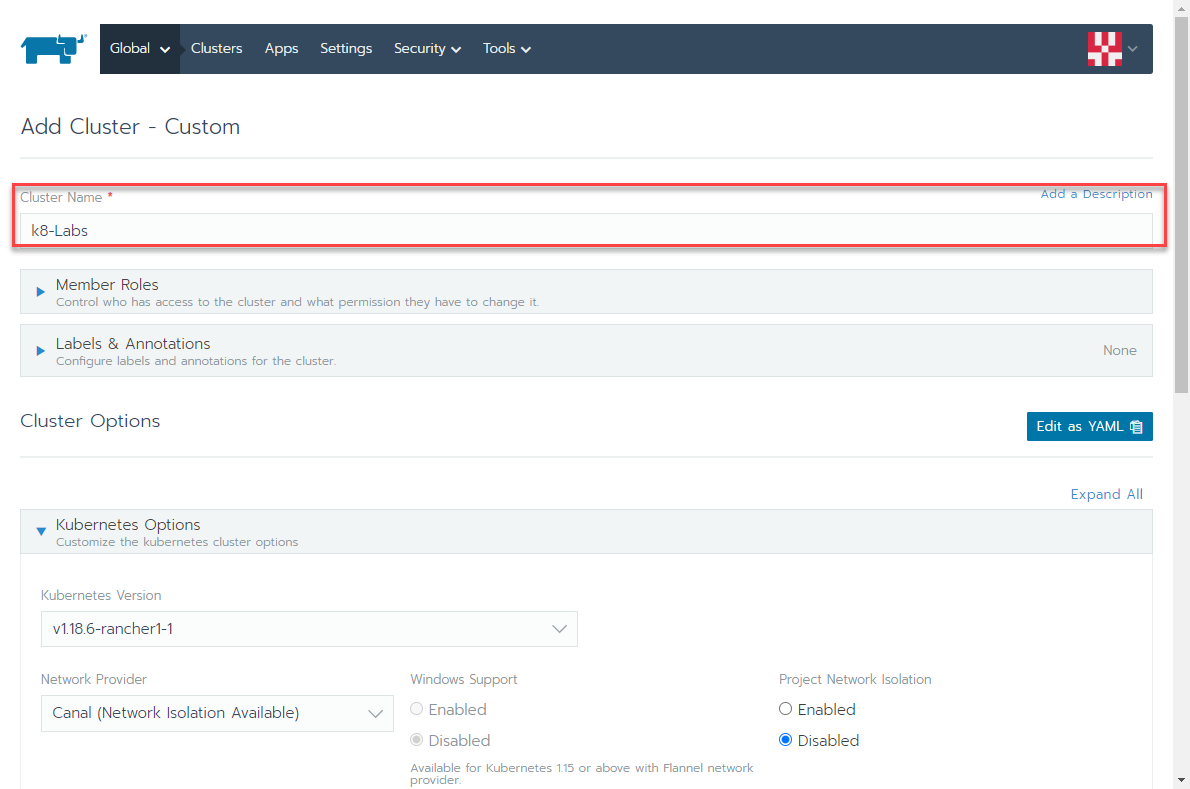
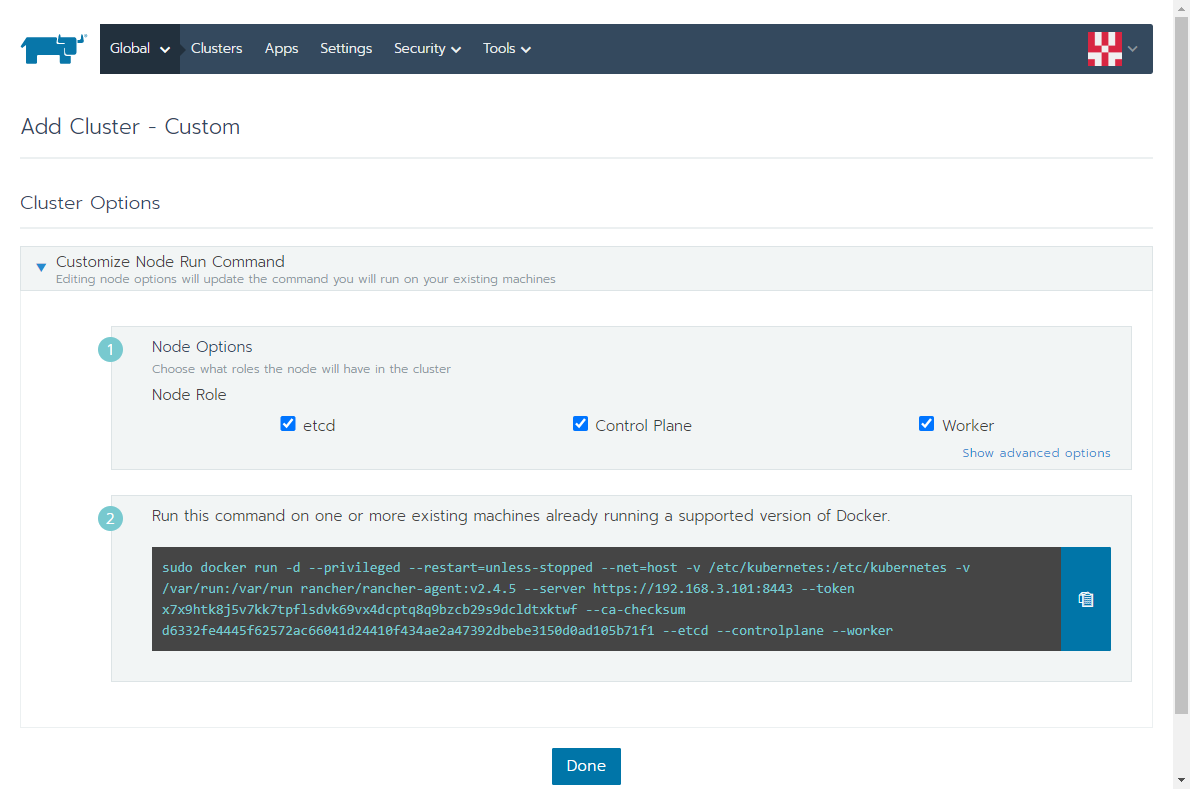
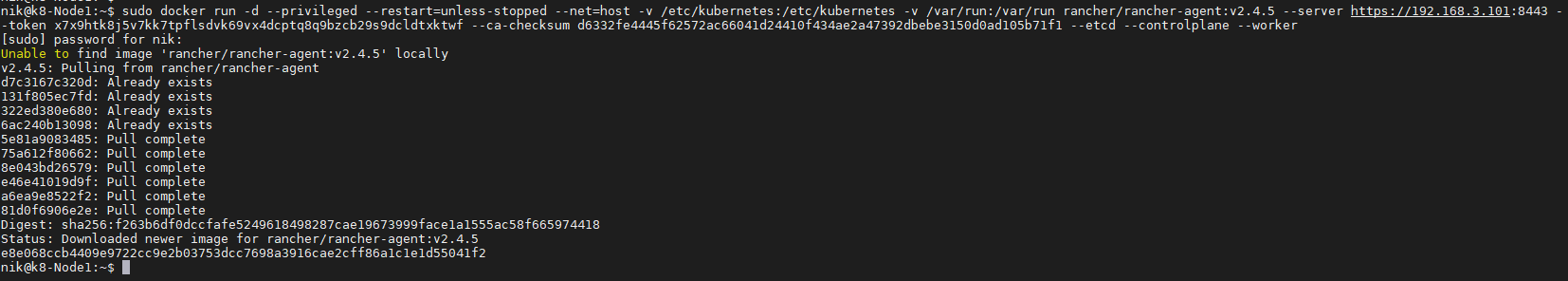
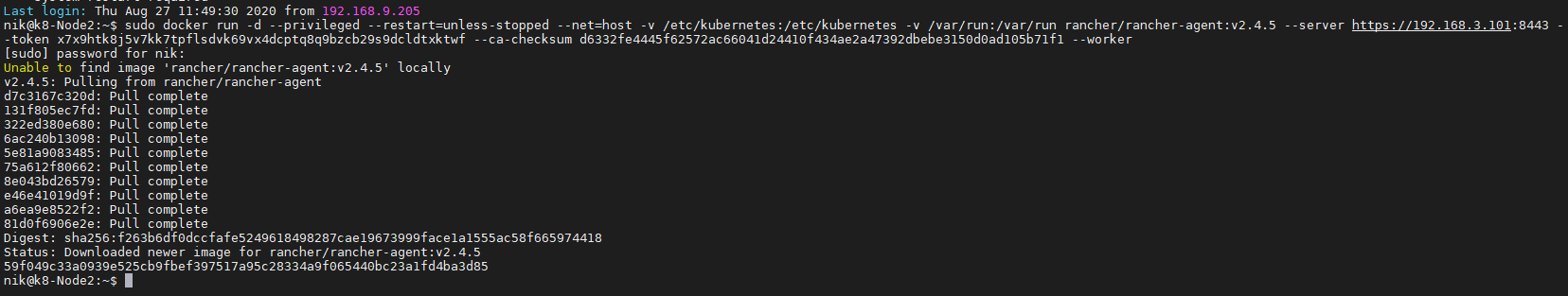
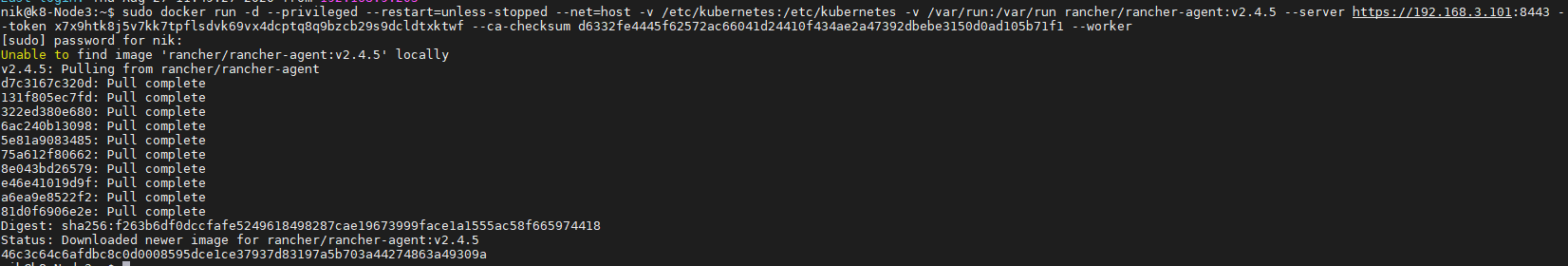
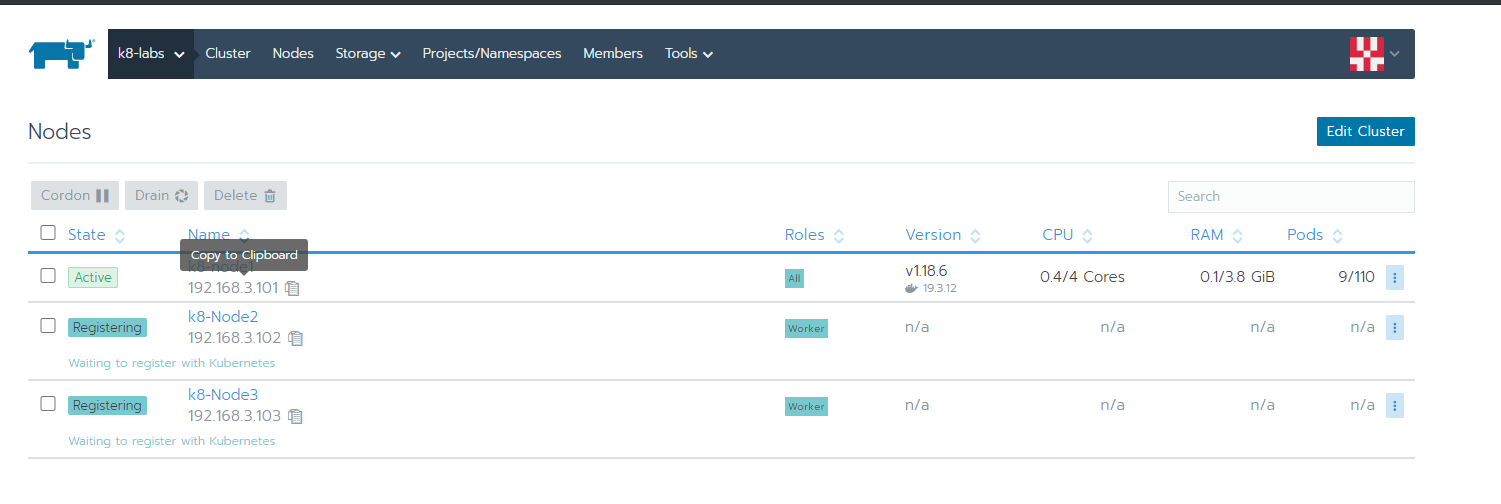
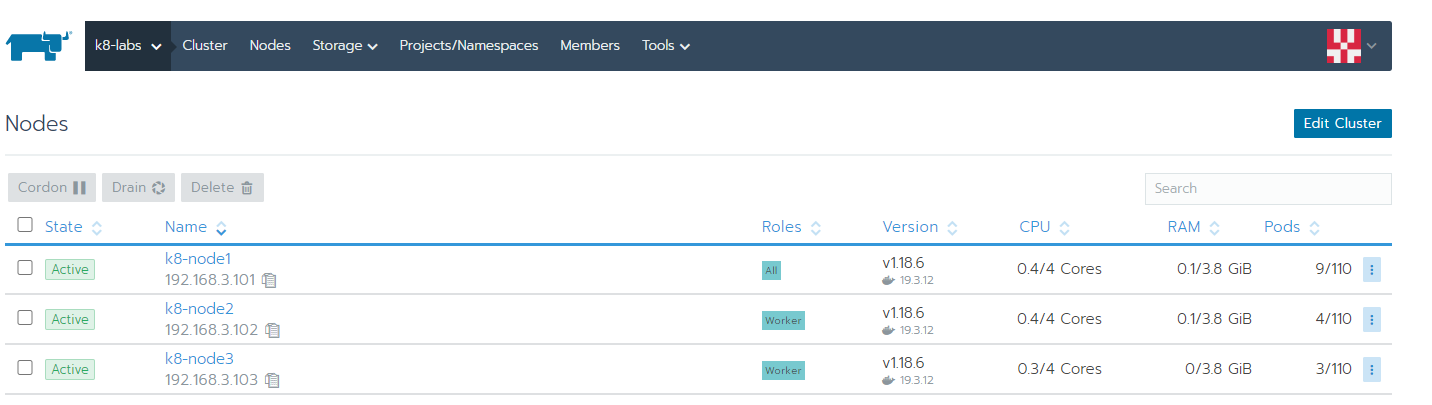
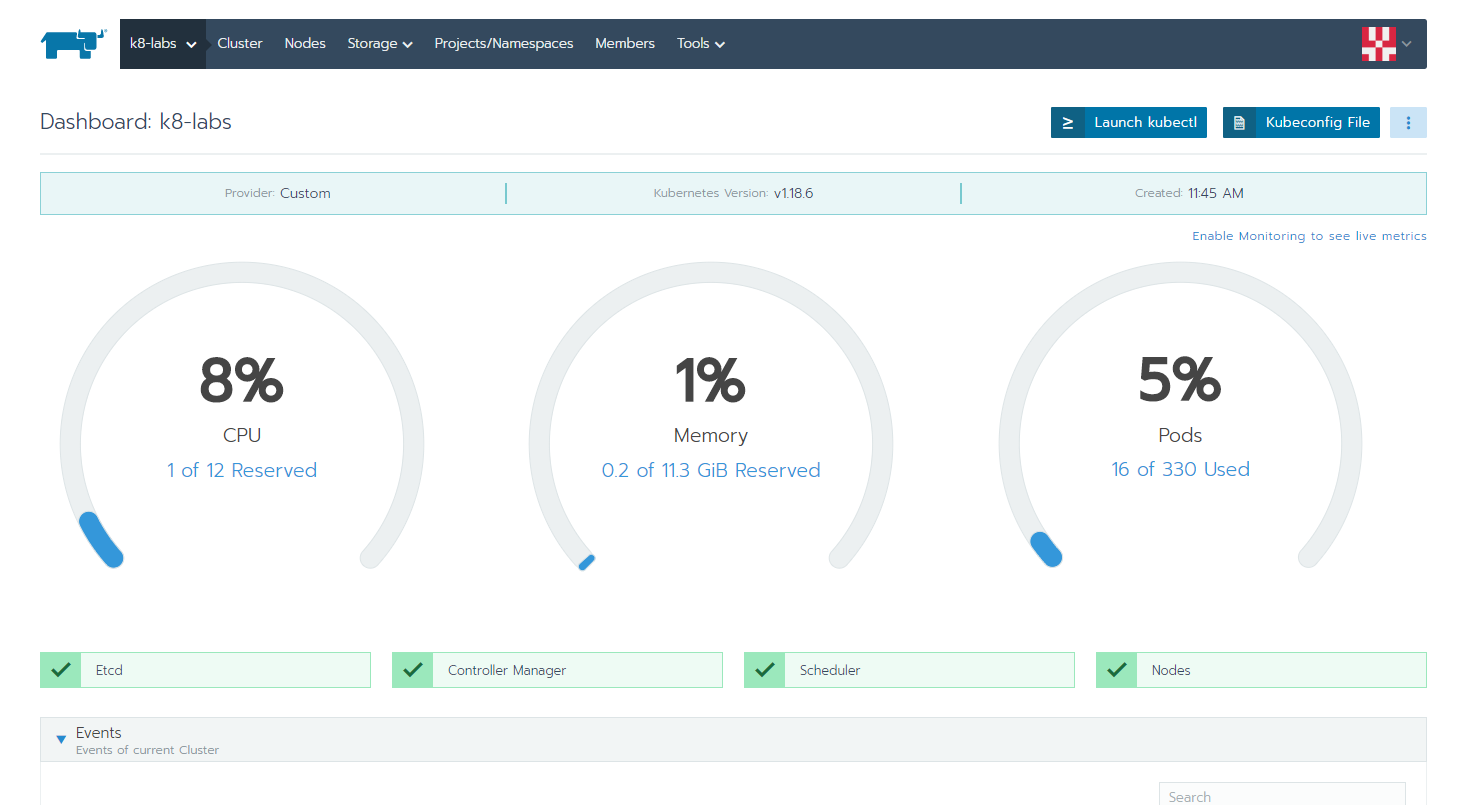
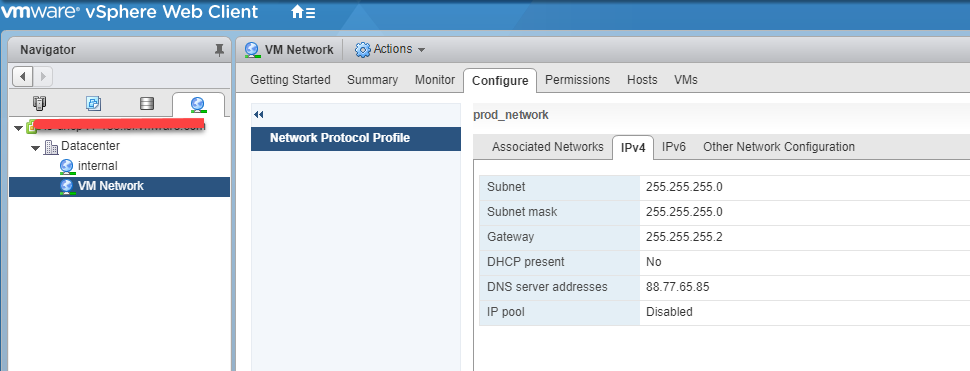
create a symlnk of the snap package to the deepin desktop config dir
sudo ln -s /var/lib/snapd/desktop/applications/sublime-text_subl.desktop /usr/share/applications/sublime-text_subl.desktop
below example to make it executable globally
sudo ln -s /snap/bin/bashtop /usr/sbin/bashtop