screenshot:

log: /var/log/boot.gz
no PCI ACS support device_idworkaround was to disable ACS
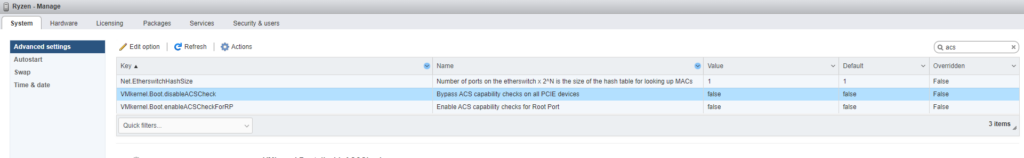
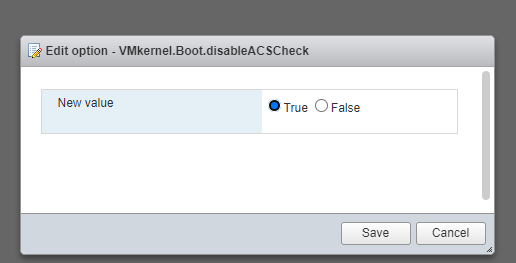
screenshot:

log: /var/log/boot.gz
no PCI ACS support device_idworkaround was to disable ACS


screenshot:
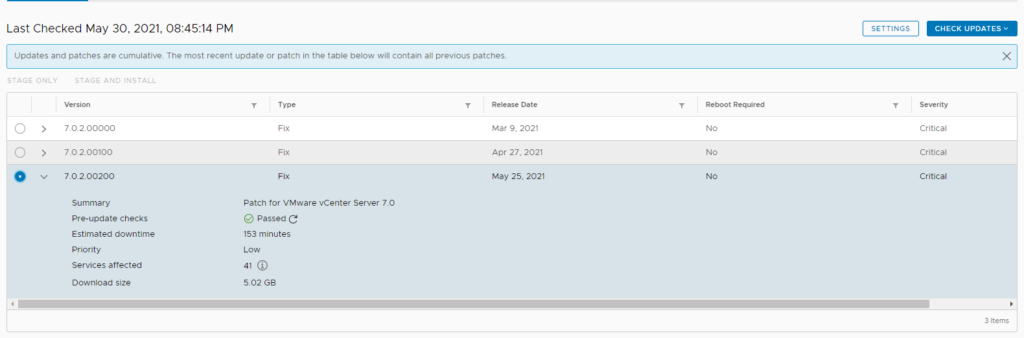
Solution: remove/rename the software update status config file
mv /etc/applmgmt/appliance/software_update_state.conf /etc/applmgmt/appliance/software_update_state.conf.bak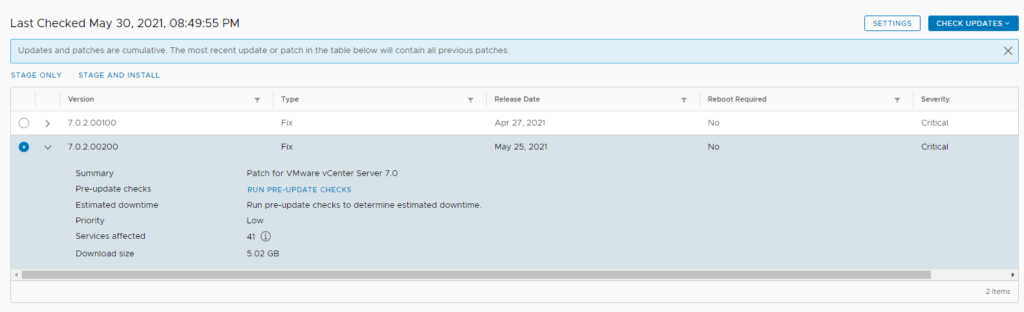
On a side note: I ran into the issue after attempting to “stage and install” my homelabs vcsa,
logs reveal:
/var/log/vmware/applmgmt/applmgmt.log
2021-05-30T15:20:26.108 [3758]DEBUG:vmware.appliance.update.update_functions:Removing the mount point /mnt/iso-contents
2021-05-30T15:20:26.109 [3758]INFO:vmware.appliance.update.update_functions:ISO unmounted successfully
2021-05-30T15:20:26.109 [3758]DEBUG:vmware.appliance.update.update_b2b:discoverLocalUpdate failed.
Traceback (most recent call last):
File "/usr/lib/applmgmt/update/py/vmware/appliance/update/update_b2b.py", line 1434, in _discoverUpdateAt
tempFolder)
File "/usr/lib/python3.7/shutil.py", line 248, in copy
copyfile(src, dst, follow_symlinks=follow_symlinks)
File "/usr/lib/python3.7/shutil.py", line 120, in copyfile
with open(src, 'rb') as fsrc:
FileNotFoundError: [Errno 2] No such file or directory: '/mnt/iso-contents/manifest-latest.xml'
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "/usr/lib/applmgmt/update/py/vmware/appliance/update/update_b2b.py", line 1640, in discoverLocalUpdatesNoException
_discoverLocalUpdates()
File "/usr/lib/applmgmt/update/py/vmware/appliance/update/update_b2b.py", line 1631, in _discoverLocalUpdates
_discoverUpdateAtIso()
File "/usr/lib/applmgmt/update/py/vmware/appliance/update/update_b2b.py", line 1607, in _discoverUpdateAtIso
raise e
File "/usr/lib/applmgmt/update/py/vmware/appliance/update/update_b2b.py", line 1602, in _discoverUpdateAtIso
_discoverUpdateAt(manifestDir, packagesDir, copyFileFunc, 'iso')
File "/usr/lib/applmgmt/update/py/vmware/appliance/update/update_b2b.py", line 1446, in _discoverUpdateAt
raise RpmManifestNotFoundException
vmware.appliance.update.update_b2b.RpmManifestNotFoundException
so, I did the above, staged the upgrade repository this time:

Then ran the install:

VMware Content library, A unique way to make VM templates/ISO’s available across multiple vCenter’s. However, It does not handle Datacenter segregation very well when storing the contents on NFS/VMFS.
A subscribed library would need dedicated storage space and would be pointless in my setup as I had presented the NFS volume to all host.
I have an NFS volume presented across all the host across several Data center. Although the NFS UUID and the name of the datastore are the same (ISO), on the vCenter database, this is stored with a different datacenter ID as they are segregated by the datacenter object.
id | name | datacenter_id
-----+----------------+---------------
157 | Template | 77
158 | SlowBro_400 | 77
159 | ISO | 77
160 | SharedLUN | 77
161 | 10.154 | 77
156 | template | 77
13 | SlowBro_legasy | 2
14 | 10.128 | 2
91 | ISO | 2
16 | Template | 2
92 | is-tse-d129_1 | 2
12 | SlowBro_400 | 2VCDB=# select * from vpx_entity where id=77;
id | name | type_id | parent_id
----+--------------+---------+-----------
77 | BLR | 8 | 1
(1 row)
VCDB=# select * from vpx_entity where id=2;
id | name | type_id | parent_id
----+------------+---------+-----------
2 | HYD | 8 | 1
(1 row)With this configuration, When I had created a content library, as per the db, this was only referencing to once of the site datastore, IE: we only see iso (id 159) from BLR (id 77) datacenter.
What this means is The content library objects can only be deployed to one of the datacenter rather than being able to deploy them across all datacenter’s on the vCenter.
VCDB=# select * from cl_storage;
id | storageuri | type
--------------------------------------+--------------------------------------------------------------+-----------
a0018db8-f630-4c04-b0f1-30c900ad691c | Datastore:datastore-159:481639ff-d88d-4622-8872-ec6856e6b157 | Datastore
bf8e8dcb-5b28-4b03-863e-89308bc8c501 | Datastore:datastore-157:481639ff-d88d-4622-8872-ec6856e6b157 | Datastore
The above table references:
VCDB=# select * from cl_library_storage;
library_id | storage_id
--------------------------------------+--------------------------------------
3336e2ad-8166-4e6a-850d-a9d81c41ba01 | a0018db8-f630-4c04-b0f1-30c900ad691c
946cea65-5cd0-41e0-83ab-17259f690ce1 | bf8e8dcb-5b28-4b03-863e-89308bc8c501So.. Logically, If I add the other ID for ISO on this table cl_storage and create a referencing record in cl_library_storage then we should be able to use the same content library across all datacenter.
The ID from the above must be unique and must match the two tables. I added the below records (i added another record by incrementing one of the values after the co-relating table.
after change
VCDB=# select * from cl_storage;
id | storageuri | type
--------------------------------------+--------------------------------------------------------------+-----------
a0018db8-f630-4c04-b0f1-30c900ad691c | Datastore:datastore-159:481639ff-d88d-4622-8872-ec6856e6b157 | Datastore
bf8e8dcb-5b28-4b03-863e-89308bc8c501 | Datastore:datastore-157:481639ff-d88d-4622-8872-ec6856e6b157 | Datastore
bf8e8dcb-5b28-4b03-863e-89308bc8c502 | Datastore:datastore-11:481639ff-d88d-4622-8872-ec6856e6b157 | Datastore
VCDB=# select * from cl_library_storage;
library_id | storage_id
--------------------------------------+--------------------------------------
3336e2ad-8166-4e6a-850d-a9d81c41ba01 | a0018db8-f630-4c04-b0f1-30c900ad691c
946cea65-5cd0-41e0-83ab-17259f690ce1 | bf8e8dcb-5b28-4b03-863e-89308bc8c501
946cea65-5cd0-41e0-83ab-17259f690ce1 | bf8e8dcb-5b28-4b03-863e-89308bc8c502after adding the above records, I am now able to deploy VM’s from the content library across Datacenters.
content library DB schema can be found here:
/usr/lib/vmware-content-library/support/scripts/db/PostgreSQL/cls_unified/cls60.sqlOkay, so the other day I had someone reach out to me for a vCenter rest API issue, Apparently, REST API to any vCenter component using the API explorer or the CLI would return the error
com.vmware.vapi.rest.httpNotFoundCli: Generate session: (on bash shell): (or simply go grab the complete command from the API explorer)
**edit the below**
VC_ADDRESS=vcenter.domain.local
[email protected]
VC_PASSWORD=password
**do not change the below***
curl -u "$VC_USER:$VC_PASSWORD" \
-X POST \
-k --cookie-jar cookies.txt \
"https://$VC_ADDRESS/rest/com/vmware/cis/session"
**the cookies file should now have a sessionID, use this session in the upcomeing commands*** test VAPI using bash
root@nvcsa-01 [ /tmp ]# curl -X GET --header 'Accept: application/json' --header 'vmware-api-session-id: 71b32ba6c59bc4bc284757b2a0d6e525' 'https://vcsa/rest/vcenter/cluster'
{"name":"com.vmware.vapi.rest.httpNotFound","localizableMessages":[{"defaultMessage":"Not found.","id":"com.vmware.vapi.rest.httpNotFound"}],"majorErrorCode":404}rat this time clearly, something is wrong. Looking at the URL: https://vcsa_URL/rest/vcenter
Looking at the rhttp configuration:
root@VCSA [ /etc/vmware-rhttpproxy/endpoints.conf.d ]# grep rest *.conf
vapi-endpoint.conf:/rest local 12346 redirect allow
vapi-endpoint.conf:/site/rest local 12346 redirect allow
Looking at the process:
root@vcsa [ /etc/vmware-rhttpproxy/endpoints.conf.d ]# netstat -anop | grep -i listen | grep 12346
tcp6 0 0 ::1:12346 :::* LISTEN 11956/vmware-vapi-e off (0.00/0/0)
tcp6 0 0 127.0.0.1:12346 :::* LISTEN 11956/vmware-vapi-e off (0.00/0/0)
So it is clear that the service responsible for REST is vapi and the service is running.
looking at the logs did not reveal anything out of the ordinary. in fact it reported nothing. aside from the below
2019-11-27T02:45:19.623+08:00 | INFO | state-manager1 | DefaultStateManager | Invoking http-server
2019-11-27T02:45:19.624+08:00 | INFO | state-manager1 | BaseServerBuilder | Creating endpoint with name 'default' on address(es): 127.0.0.1, ::1 with port: 12346
2019-11-27T02:45:19.682+08:00 | WARN | state-manager1 | BaseServerBuilder | Failed to bind /0:0:0:0:0:0:0:1:12346 while testing the endpoint validity
java.net.SocketException: Protocol family unavailable
at java.net.PlainSocketImpl.socketBind(Native Method)
at java.net.AbstractPlainSocketImpl.bind(AbstractPlainSocketImpl.java:387)
at java.net.Socket.bind(Socket.java:644)
at com.vmware.vapi.endpoint.http.BaseServerBuilder.isPortAccessible(BaseServerBuilder.java:172)
at com.vmware.vapi.endpoint.http.BaseServerBuilder.trimInvalidEndpoints(BaseServerBuilder.java:147)
at com.vmware.vapi.endpoint.http.BaseServerBuilder.populateEndpointSettings(BaseServerBuilder.java:183)
at com.vmware.vapi.endpoint.http.BaseServerBuilder.createServer(BaseServerBuilder.java:233)
at com.vmware.vapi.endpoint.http.BaseServerBuilder.buildInitial(BaseServerBuilder.java:75)
at com.vmware.vapi.state.impl.DefaultStateManager.build(DefaultStateManager.java:354)
at com.vmware.vapi.state.impl.DefaultStateManager$1.doInitialConfig(DefaultStateManager.java:168)
at com.vmware.vapi.state.impl.DefaultStateManager$1.run(DefaultStateManager.java:151)
at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:511)
at java.util.concurrent.FutureTask.run(FutureTask.java:266)
at java.util.concurrent.ScheduledThreadPoolExecutor$ScheduledFutureTask.access$201(ScheduledThreadPoolExecutor.java:180)
at java.util.concurrent.ScheduledThreadPoolExecutor$ScheduledFutureTask.run(ScheduledThreadPoolExecutor.java:293)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624)
at java.lang.Thread.run(Thread.java:748)okay, so this made clear to me that the application “default” had problems with a port bind, (bind /0:0:0:0:0:0:0:1:12346), so I took a look at the configuration file /etc/vmware-vapi/endpoint.properties, removed the ::1 from the config (I don’t think this is a problem TBH since all the other web apps load up and is accessible via rest)

So I bumped up the VAPI logging (instructions here) and found the below
Looking deeper at the logs with trivia enabled, I found the below when the REST calls failed:
2019-11-27T04:21:10.398+08:00 | DEBUG | vAPI-I/O dispatcher-1 | JsonServerConnection | Sending JSON response of size 50
2019-11-27T04:21:21.213+08:00 | DEBUG | jetty-default-35 | RequestDispatcher | method=GET, uriInfo=/vcenter/datacenter
2019-11-27T04:21:21.214+08:00 | DEBUG | jetty-default-35 | UriLocatorImpl | Matched uriTemplates are not found for requesturi = /vcenter/datacenter
2019-11-27T04:21:21.215+08:00 | DEBUG | jetty-default-35 | RestMainServlet | Failed to process request.
RestException [majorErrorCode=404, messageId=com.vmware.vapi.rest.MessageId@1721d534, params=[], message=null]
at com.vmware.vapi.rest.RequestDispatcher.dispatch(RequestDispatcher.java:64)
at com.vmware.vapi.endpoint.servlet.rest.RestMainServlet.service(RestMainServlet.java:44)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:790)
at com.vmware.vapi.endpoint.common.ProxyServlet.service(ProxyServlet.java:50)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:790)
at org.eclipse.jetty.servlet.ServletHolder.handle(ServletHolder.java:812)
at org.eclipse.jetty.servlet.ServletHandler$CachedChain.doFilter(ServletHandler.java:1669)
at org.eclipse.jetty.servlets.DoSFilter.doFilterChain(DoSFilter.java:471)
at org.eclipse.jetty.servlets.DoSFilter.doFilter(DoSFilter.java:323)
at org.eclipse.jetty.servlets.DoSFilter.doFilter(DoSFilter.java:293)
at org.eclipse.jetty.servlet.ServletHandler$CachedChain.doFilter(ServletHandler.java:1652)
at com.vmware.vapi.endpoint.http.RequestSizeFilter.doFilter(RequestSizeFilter.java:59)
at org.eclipse.jetty.servlet.ServletHandler$CachedChain.doFilter(ServletHandler.java:1652)
at org.eclipse.jetty.servlet.ServletHandler.doHandle(ServletHandler.java:585)
at org.eclipse.jetty.server.handler.ScopedHandler.handle(ScopedHandler.java:143)
at org.eclipse.jetty.security.SecurityHandler.handle(SecurityHandler.java:577)
at org.eclipse.jetty.server.session.SessionHandler.doHandle(SessionHandler.java:223)
at org.eclipse.jetty.server.handler.ContextHandler.doHandle(ContextHandler.java:1127)
at org.eclipse.jetty.servlet.ServletHandler.doScope(ServletHandler.java:515)
at org.eclipse.jetty.server.session.SessionHandler.doScope(SessionHandler.java:185)
at org.eclipse.jetty.server.handler.ContextHandler.doScope(ContextHandler.java:1061)
at org.eclipse.jetty.server.handler.ScopedHandler.handle(ScopedHandler.java:141)
at org.eclipse.jetty.server.handler.HandlerList.handle(HandlerList.java:52)
at org.eclipse.jetty.server.handler.HandlerWrapper.handle(HandlerWrapper.java:97)
at org.eclipse.jetty.server.Server.handle(Server.java:499)
at org.eclipse.jetty.server.HttpChannel.handle(HttpChannel.java:311)
at org.eclipse.jetty.server.HttpConnection.onFillable(HttpConnection.java:258)
at org.eclipse.jetty.io.AbstractConnection$2.run(AbstractConnection.java:544)
at org.eclipse.jetty.util.thread.QueuedThreadPool.runJob(QueuedThreadPool.java:635)
at org.eclipse.jetty.util.thread.QueuedThreadPool$3.run(QueuedThreadPool.java:555)
at java.lang.Thread.run(Thread.java:748)Okay, so now we are getting somewhere. “Matched uriTemplates are not found for requesturi = /vcenter/datacenter”
I quickly installed jxplorer and reviewed the endpoints for vApi (configuration>site>%site_name%>lookupService>ServiceRegisteration)
Basically, I was looking for the endpoints registered as serviceType.product=com.vmware.cis serviceType.type=cs.vapi
Basically, you wanna look for an endpoint type: .protocol=vapi.json.http and ID com.vmware.vapi.vcenter under the vCenter’s vapi instance similar to the below which was missing on the problematic vCenter.

note that the endpoint name does not really matter. On the problematic vCenter, there existed endpoint9 but it was for a different endpoint.
So what is the difference?
I quickly grabbed the service ID for vApi service for both the working and nonworking instance as a spec using the below command: (replace the id with the service ID on your instance)
/usr/lib/vmidentity/tools/scripts/lstool.py get --url "https://localhost/lookupservice/sdk" --id "f8ab1f69-c73a-4d94-9ac8-7bf85308954e" --no-check-cert --as-spec > /tmp/spec.txII observed the below endpoint where missing on the broken vCenter:
endpoint9.type.id=com.vmware.vapi.vcenter <----------------------------
endpoint9.url=http://localhost:12346/vcenter
endpoint9.ssltrust0=
endpoint9.data0.key=com.vmware.vapi.metadata.authentication.remote
endpoint9.data0.value=http://localhost:12346/vcenter
endpoint9.data1.key=com.vmware.vapi.metadata.metamodel.remote
endpoint9.data1.value=http://localhost:12346/vcenter
endpoint9.data2.key=com.vmware.vapi.metadata.cli.remote
endpoint9.data2.value=http://localhost:12346/vcenterOn the broken vCenter VAPi endpoint spec, I added the above as endpoint12 (11 was in use), Saved the file and re-imported it back in using the below command
/usr/lib/vmidentity/tools/scripts/lstool.py reregister --spec spec.txt --url https://localhost/lookupservice/sdk --user [email protected] --password "Admin!23" --id "f8ab1f69-c73a-4d94-9ac8-7bf85308954e" --no-check-certNote that the value for “endpoint9.ssltrust0=” should be filled up with the contents found in the spec file
Restarted the VAPI service and VOLA! Rest API for vCenter started to work!!!!
cp /etc/vmware-vapi/endpoint-log4j.properties endpoint-log4j.properties.bak
sed -i -e 's/INFO/trivia/g' /etc/vmware-vapi/endpoint-log4j.properties
log files: /var/log/vmware/vapi/endpoint/endpoint.log
Start TFTP service
service atftpd startAllow TFTP port on the VCSA firewall
iptables -A port_filter -m state --state New -i eth0 -p udp --dport 69 -j ACCEPT
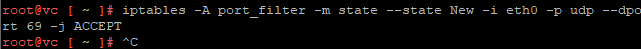
Confirm if the port is allowed on the firewall
iptables -nL | grep 69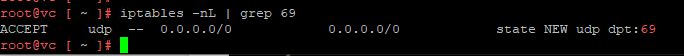
Make the firewall rules persistent:
Export Ip tables rule
iptables-save > /etc/iptables.rulesCreate a startup script at path: /etc/init.d/startftp.sh with the below contents:
#! /bin/sh
#
# TFTP Start/Stop the TFTP service and allow port 69
#
# chkconfig: 345 80 05
# description: atftpd
### BEGIN INIT INFO
# Provides: atftpd
# Required-Start: $local_fs $remote_fs $network
# Required-Stop:
# Default-Start: 3 5
# Default-Stop: 0 1 2 6
# Description: TFTP
### END INIT INFO
service atftpd start
iptables-restore -c < /etc/iptables.ruleschange the permissions of the script
chmod +x /etc/init.d/startftp.shset the script to run during startup:
chkconfig --add /etc/init.d/startftp.shcopy the contents of TFTP from autodeploy_zip to /var/lib/tftpboot
Copy Table to CSV
copy vpx_vm to '/tmp/vpx_vm' DELIMITER ',' CSV;
Copy table from CSV
copy table FROM '/tmp/table.csv' DELIMITER ',' CSV;list Top tables by size:
SELECT
schema_name,
relname,
pg_size_pretty(table_size) AS size,
table_size
FROM (
SELECT
pg_catalog.pg_namespace.nspname AS schema_name,
relname,
pg_relation_size(pg_catalog.pg_class.oid) AS table_size
FROM pg_catalog.pg_class
JOIN pg_catalog.pg_namespace ON relnamespace = pg_catalog.pg_namespace.oid
) t
WHERE schema_name NOT LIKE 'pg_%'
ORDER BY table_size DESC;postgres password:
root@is-dhcp34-161 [ / ]# cat ~/.pgpass
localhost:5432:replication:replicator:*v&w1pTkmZY}Q2<z
127.0.0.1:5432:replication:replicator:*v&w1pTkmZY}Q2<z
/var/run/vpostgres:5432:replication:replicator:*v&w1pTkmZY}Q2<z
localhost:5432:postgres:postgres:_ouG|OZ4NUwna0fB
127.0.0.1:5432:postgres:postgres:_ouG|OZ4NUwna0fB
localhost:5432:VCDB:postgres:_ouG|OZ4NUwna0fB
127.0.0.1:5432:VCDB:postgres:_ouG|OZ4NUwna0fB
/var/run/vpostgres:5432:VCDB:postgres:_ouG|OZ4NUwna0fB
/var/run/vpostgres:5432:postgres:postgres:_ouG|OZ4NUwna0fRename table
ALTER TABLE tablename RENAME TO new_table;Database backup/Dump using pg_dump
pg_dump VCDB -U postgres > /tmp/dump
Database backup (excluding a specific corrupted table)
pg_dump VCDB -U postgres -T vpx_host > /tmp/dump.excluting.currupt.table
Note: T: Exclude table and grab the rest.
t: backup specific table only.Determining broken tables(pg toast)
for ((i=0; i<"668"; i++ )); do /opt/vmware/vpostgres/current/bin/psql -U "postgres" "VCDB" -c "SELECT * FROM VPX_VM LIMIT 1 offset $i" >/dev/null || echo $i; done
Note: Replace 668 with the highest table count on your setupStarting postgres in single user mode:
su - postgres –c postgres --single -D /storage/db/vpostgres
use below to fix checksum on start
su - postgres –c /path_to_postgres/postgres --single -D /storage/db/vpostgres -c fix_block_checksum="1663/1636/1694/0/978"
Note: Postgres will only start as the user postgres. ignoring the su - postgres will likely cause the service to failReset WAL (Write Ahead logs)
pg_resetxlog /storage/db/vpostgresError “MultiXactId has not been created yet — apparent wraparound”
VACUUM FREEZE table_name; Manual Recovery of corrupt records from a postgres table.
A bash while loop that creates an SQL file to export every row individually into individual files. The rows with corrupt records are skipped.
you will need a unique readable collum. For the below example I have exported surr_id from vpx_text_array as /tmp/SURR_KEY_vpx_text_array and use a while loop to create individual lines for export on the .SQL file
while read p; do echo "copy (select * from vpx_text_array where surr_key=$p) to '/db/$p' delimiter ',' csv;" >> /db/out.sql; done < /tmp/SURR_KEY_vpx_text_array
Use psql commandline to invoke the SQL script
/opt/vmware/vpostgres/9.4/bin/psql -U postgres -d VCDB -a -f /db/out.sql >> /db.export.err
psql.bin:/db/out.sql:153: ERROR: missing chunk number 0 for toast value 66095 in pg_toast_19389 <----currupt records. TBR from other tables
psql.bin:/db/out.sql:190: ERROR: missing chunk number 0 for toast value 66096 in pg_toast_19389 <----currupt records. TBR from other tables
Query to list top events from the events DB.
SELECT COUNT(EVENT_ID) AS NUMEVENTS, EVENT_TYPE, USERNAME FROM VPXV_EVENT_ALL GROUP BY EVENT_TYPE, USERNAME ORDER BY NUMEVENTS DESC LIMIT 10;
DB schema paths
VCDB:
VUMDB: /usr/lib/vmware-updatemgr/share/VCI_base_postgresql.sql If the vCenter was upgraded from 5.5, it retains legacy endpoints for lookup service
IE: https://FQDN:7444/lookupservce/sdk
Running certificate-manager will not replace the certificate and vCenter might actually start to complain about expired certificate although they are valid.
In this can be easily worked around by replacing the certificate on the VECS store:
Start by exporting the STS_INTERNAL_SSL_CERT and MACHINE_SSL_CERT
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --store MACHINE_SSL_CERT --alias __MACHINE_CERT --output /ssl/machine_ssl.crt
/usr/lib/vmware-vmafd/bin/vecs-cli entry getkey --store MACHINE_SSL_CERT --alias __MACHINE_CERT --output /ssl/machine_ssl.key
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --store STS_INTERNAL_SSL_CERT --alias __MACHINE_CERT --output /ssl/STS_INTERNAL_SSL_CERT-__MACHINE_CERT.crt
/usr/lib/vmware-vmafd/bin/vecs-cli entry getkey --store STS_INTERNAL_SSL_CERT --alias __MACHINE_CERT --output /ssl/STS_INTERNAL_SSL_CERT-__MACHINE_CERT.keyDelete the contents of STS_INTERNAL_SSL_CERT store
/usr/lib/vmware-vmafd/bin/vecs-cli entry delete --store STS_INTERNAL_SSL_CERT --alias __MACHINE_CERT -y
import machine_ssl store to the STS store:
/usr/lib/vmware-vmafd/bin/vecs-cli entry create --store STS_INTERNAL_SSL_CERT --alias __MACHINE_CERT --cert /ssl/machine_ssl.crt --key /ssl/machine_ssl.key Restart services and confirm service status
VMCA is the Default self-signed certificates that
All solution users and machine SSL certificates are signed with this certificate.
VMCA certificates can be regenerated by using option 8 on the
root@is-dhcp36-107 [ / ]# /usr/lib/vmware-vmca/bin/certificate-manager
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
| |
| *** Welcome to the vSphere 6.5 Certificate Manager *** |
| |
| -- Select Operation -- |
| |
| 1. Replace Machine SSL certificate with Custom Certificate |
| |
| 2. Replace VMCA Root certificate with Custom Signing |
| Certificate and replace all Certificates |
| |
| 3. Replace Machine SSL certificate with VMCA Certificate |
| |
| 4. Regenerate a new VMCA Root Certificate and |
| replace all certificates |
| |
| 5. Replace Solution user certificates with |
| Custom Certificate |
| |
| 6. Replace Solution user certificates with VMCA certificates |
| |
| 7. Revert last performed operation by re-publishing old |
| certificates |
| |
| 8. Reset all Certificates |
|_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _|
Note : Use Ctrl-D to exit.
Option[1 to 8]:
choosing option 8, you are presented with the below options:
Option[1 to 8]: 8
Do you wish to generate all certificates using configuration file : Option[Y/N] ? : y
Please provide valid SSO and VC priviledged user credential to perform certificate operations.
Enter username [[email protected]]:[email protected]
Enter password:
Please configure certool.cfg with proper values before proceeding to next step.
Press Enter key to skip optional parameters or use Default value.
Enter proper value for 'Country' [Default value : US] :
Enter proper value for 'Name' [Default value : CA] :
Enter proper value for 'Organization' [Default value : VMware] :
Enter proper value for 'OrgUnit' [Default value : VMware Engineering] :
Enter proper value for 'State' [Default value : California] :
Enter proper value for 'Locality' [Default value : Palo Alto] :
Enter proper value for 'IPAddress' (Provide comma separated values for multiple IP addresses) [optional] :
Enter proper value for 'Email' [Default value : [email protected]] :
Enter proper value for 'Hostname' (Provide comma separated values for multiple Hostname entries) [Enter valid Fully Qualified Domain Name(FQDN), For Example : example.domain.com] : is-dhcp36-107.isl.vmware.com
Enter proper value for VMCA 'Name' :VMCA
Continue operation : Option[Y/N] ? : y
You are going to reset by regenerating Root Certificate and replace all certificates using VMCA
Continue operation : Option[Y/N] ? : y
Below are the .cfg’s created for the certificate
root@is-dhcp36-107 [ /var/tmp/vmware ]# ls -ltrh
total 32K
drwxr-xr-x 3 root root 4.0K Mar 14 00:07 cis-license
-rw-r--r-- 1 root root 191 Apr 2 19:24 certool.cfg
-rw-r--r-- 1 root root 243 Apr 2 19:24 vsphere-webclient.cfg
-rw-r--r-- 1 root root 240 Apr 2 19:24 vpxd-extension.cfg
-rw-r--r-- 1 root root 230 Apr 2 19:24 vpxd.cfg
-rw-r--r-- 1 root root 87 Apr 2 19:24 root.cfg
-rw-r--r-- 1 root root 217 Apr 2 19:24 MACHINE_SSL_CERT.cfg
-rw-r--r-- 1 root root 233 Apr 2 19:24 machine.cfg
Workflow (below are the commands that are run in the background)
/usr/lib/vmware-vmafd/bin/dir-cli service list --login [email protected] --password *****
1. machine-6368669f-591a-44fa-bfb3-a76b166bfed6
2. vsphere-webclient-6368669f-591a-44fa-bfb3-a76b166bfed6
3. vpxd-6368669f-591a-44fa-bfb3-a76b166bfed6
4. vpxd-extension-6368669f-591a-44fa-bfb3-a76b166bfed6
root@is-dhcp36-107 [ /var/tmp/vmware ]# cat root.cfg
Country = US
Name = VMCA
OrgUnit = VMware Engineering
State = California
#IPAddress =
root@is-dhcp36-107 [ /var/tmp/vmware ]# cat machine.cfg
Country = US
Name = machine-6368669f-591a-44fa-bfb3-a76b166bfed6
Organization = VMware
OrgUnit = VMware Engineering
State = California
Locality = Palo Alto
#IPAddress =
Email = [email protected]
Hostname = is-dhcp36-107.isl.vmware.com
root@is-dhcp36-107 [ /var/tmp/vmware ]# cat vsphere-webclient.cfg
Country = US
Name = vsphere-webclient-6368669f-591a-44fa-bfb3-a76b166bfed6
Organization = VMware
OrgUnit = VMware Engineering
State = California
Locality = Palo Alto
#IPAddress =
Email = [email protected]
Hostname = is-dhcp36-107.isl.vmware.com
root@is-dhcp36-107 [ /var/tmp/vmware ]# cat vpxd.cfg
Country = US
Name = vpxd-6368669f-591a-44fa-bfb3-a76b166bfed6
Organization = VMware
OrgUnit = VMware Engineering
State = California
Locality = Palo Alto
#IPAddress =
Email = [email protected]
Hostname = is-dhcp36-107.isl.vmware.com
root@is-dhcp36-107 [ /var/tmp/vmware ]# cat vpxd-extension.cfg
Country = US
Name = vpxd-extension-6368669f-591a-44fa-bfb3-a76b166bfed6
Organization = VMware
OrgUnit = VMware Engineering
State = California
Locality = Palo Alto
#IPAddress =
Email = [email protected]
Hostname = is-dhcp36-107.isl.vmware.com
root@is-dhcp36-107 [ /var/tmp/vmware ]# cat MACHINE_SSL_CERT.cfg
Country = US
Name = is-dhcp36-107.isl.vmware.com
Organization = VMware
OrgUnit = VMware Engineering
State = California
Locality = Palo Alto
#IPAddress =
Email = [email protected]
Hostname = is-dhcp36-107.isl.vmware.comCheck if a backup store
/usr/lib/vmware-vmafd/bin/vecs-cli store list
MACHINE_SSL_CERT
TRUSTED_ROOTS
TRUSTED_ROOT_CRLS
machine
vsphere-webclient
vpxd
vpxd-extension
SMS
/usr/lib/vmware-vmafd/bin/vecs-cli store create --name BACKUP_STORE
service-control --start vmafdd
service-control --start vmcad
service-control --start vmdirdExport exiting certificate and import them to the backup store
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --store MACHINE_SSL_CERT --alias __MACHINE_CERT --output /var/tmp/vmware/old_machine_ssl.crt
/usr/lib/vmware-vmafd/bin/vmafd-cli get-pnid --server-name localhost
/usr/lib/vmware-vmafd/bin/vmafd-cli get-machine-id --server-name localhost
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --store MACHINE_SSL_CERT --alias __MACHINE_CERT --output /storage/certmanager/rollback/MACHINE_SSL_CERT_bkp.crt
/usr/lib/vmware-vmafd/bin/vecs-cli entry getkey --store MACHINE_SSL_CERT --alias __MACHINE_CERT --output /storage/certmanager/rollback/MACHINE_SSL_CERT_bkp.priv
/usr/lib/vmware-vmafd/bin/vecs-cli entry delete -y --store BACKUP_STORE --alias bkp___MACHINE_CERT
/usr/lib/vmware-vmafd/bin/vecs-cli entry create --store BACKUP_STORE --alias bkp___MACHINE_CERT --cert /storage/certmanager/rollback/MACHINE_SSL_CERT_bkp.crt --key /storage/certmanager/rollback/MACHINE_SSL_CERT_bkp.priv
/usr/lib/vmware-vmafd/bin/vecs-cli entry getkey --store machine --alias machine --output /storage/certmanager/rollback/machine_bkp.priv
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --store machine --alias machine --output /storage/certmanager/rollback/machine_bkp.crt
/usr/lib/vmware-vmafd/bin/vecs-cli entry delete -y --store BACKUP_STORE --alias bkp_machine
/usr/lib/vmware-vmafd/bin/vecs-cli entry create --store BACKUP_STORE --alias bkp_machine --cert /storage/certmanager/rollback/machine_bkp.crt --key /storage/certmanager/rollback/machine_bkp.priv
/usr/lib/vmware-vmafd/bin/vecs-cli entry getkey --store vsphere-webclient --alias vsphere-webclient --output /storage/certmanager/rollback/vsphere-webclient_bkp.priv
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --store vsphere-webclient --alias vsphere-webclient --output /storage/certmanager/rollback/vsphere-webclient_bkp.crt
/usr/lib/vmware-vmafd/bin/vecs-cli entry delete -y --store BACKUP_STORE --alias bkp_vsphere-webclient
/usr/lib/vmware-vmafd/bin/vecs-cli entry create --store BACKUP_STORE --alias bkp_vsphere-webclient --cert /storage/certmanager/rollback/vsphere-webclient_bkp.crt --key /storage/certmanager/rollback/vsphere-webclient_bkp.priv
/usr/lib/vmware-vmafd/bin/vecs-cli entry getkey --store vpxd --alias vpxd --output /storage/certmanager/rollback/vpxd_bkp.priv
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --store vpxd --alias vpxd --output /storage/certmanager/rollback/vpxd_bkp.crt
/usr/lib/vmware-vmafd/bin/vecs-cli entry delete -y --store BACKUP_STORE --alias bkp_vpxd
/usr/lib/vmware-vmafd/bin/vecs-cli entry create --store BACKUP_STORE --alias bkp_vpxd --cert /storage/certmanager/rollback/vpxd_bkp.crt --key /storage/certmanager/rollback/vpxd_bkp.priv
/usr/lib/vmware-vmafd/bin/vecs-cli entry getkey --store vpxd-extension --alias vpxd-extension --output /storage/certmanager/rollback/vpxd-extension_bkp.priv
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --store vpxd-extension --alias vpxd-extension --output /storage/certmanager/rollback/vpxd-extension_bkp.crt
/usr/lib/vmware-vmafd/bin/vecs-cli entry delete -y --store BACKUP_STORE --alias bkp_vpxd-extension
/usr/lib/vmware-vmafd/bin/vecs-cli entry create --store BACKUP_STORE --alias bkp_vpxd-extension --cert /storage/certmanager/rollback/vpxd-extension_bkp.crt --key /storage/certmanager/rollback/vpxd-extension_bkp.priv
Generate Machine_SSL certificate
/usr/lib/vmware-vmca/bin/certool --getrootca --server localhost
/usr/lib/vmware-vmca/bin/certool --selfca --config /var/tmp/vmware/root.cfg --server localhost
/usr/lib/vmware-vmca/bin/certool --getrootca --server localhost
/usr/lib/vmware-vmca/bin/certool --genkey --privkey=/storage/certmanager/MACHINE_SSL_CERT.priv --pubkey=/storage/certmanager/MACHINE_SSL_CERT.pub --server=localhost
/usr/lib/vmware-vmca/bin/certool --server=localhost --gencert --privkey=/storage/certmanager/MACHINE_SSL_CERT.priv --cert=/storage/certmanager/MACHINE_SSL_CERT.crt --config=/var/tmp/vmware/MACHINE_SSL_CERT.cfg
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --text --store MACHINE_SSL_CERT --alias __MACHINE_CERT
/usr/lib/vmware-vmafd/bin/vecs-cli entry delete -y --store MACHINE_SSL_CERT --alias __MACHINE_CERT
/usr/lib/vmware-vmafd/bin/vecs-cli entry list --store MACHINE_SSL_CERT
/usr/lib/vmware-vmafd/bin/vecs-cli entry create --store MACHINE_SSL_CERT --alias __MACHINE_CERT --cert /storage/certmanager/MACHINE_SSL_CERT.crt --key /storage/certmanager/MACHINE_SSL_CERT.priv
/usr/lib/vmware-vmafd/bin/vecs-cli entry list --store MACHINE_SSL_CERT
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --text --store MACHINE_SSL_CERT --alias __MACHINE_CERTGenerate machine certificate
/usr/lib/vmware-vmca/bin/certool --genkey --privkey=/storage/certmanager/machine.priv --pubkey=/storage/certmanager/machine.pub --server=localhost
/usr/lib/vmware-vmca/bin/certool --server=localhost --gencert --privkey=/storage/certmanager/machine.priv --cert=/storage/certmanager/machine.crt --config=/var/tmp/vmware/machine.cfg
/usr/lib/vmware-vmafd/bin/vmafd-cli get-machine-id --server-name localhost
/usr/lib/vmware-vmafd/bin/dir-cli service list --login [email protected] --password *****
/usr/lib/vmware-vmafd/bin/dir-cli service update --cert /storage/certmanager/machine.crt --name machine-6368669f-591a-44fa-bfb3-a76b166bfed6 --login [email protected] --password *****
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --text --store machine --alias machine
/usr/lib/vmware-vmafd/bin/vecs-cli entry delete -y --store machine --alias machine
/usr/lib/vmware-vmafd/bin/vecs-cli entry list --store machine
/usr/lib/vmware-vmafd/bin/vecs-cli entry create --store machine --alias machine --cert /storage/certmanager/machine.crt --key /storage/certmanager/machine.priv
/usr/lib/vmware-vmafd/bin/vecs-cli entry list --store machine
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --text --store machine --alias machine
Generate web client certificate
/usr/lib/vmware-vmca/bin/certool --genkey --privkey=/storage/certmanager/vsphere-webclient.priv --pubkey=/storage/certmanager/vsphere-webclient.pub --server=localhost
/usr/lib/vmware-vmca/bin/certool --server=localhost --gencert --privkey=/storage/certmanager/vsphere-webclient.priv --cert=/storage/certmanager/vsphere-webclient.crt --config=/var/tmp/vmware/vsphere-webclient.cfg
/usr/lib/vmware-vmafd/bin/vmafd-cli get-machine-id --server-name localhost
/usr/lib/vmware-vmafd/bin/dir-cli service list --login [email protected] --password *****
/usr/lib/vmware-vmafd/bin/dir-cli service update --cert /storage/certmanager/vsphere-webclient.crt --name vsphere-webclient-6368669f-591a-44fa-bfb3-a76b166bfed6 --login [email protected] --password *****
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --text --store vsphere-webclient --alias vsphere-webclient
/usr/lib/vmware-vmafd/bin/vecs-cli entry delete -y --store vsphere-webclient --alias vsphere-webclient
/usr/lib/vmware-vmafd/bin/vecs-cli entry list --store vsphere-webclient
/usr/lib/vmware-vmafd/bin/vecs-cli entry create --store vsphere-webclient --alias vsphere-webclient --cert /storage/certmanager/vsphere-webclient.crt --key /storage/certmanager/vsphere-webclient.priv
/usr/lib/vmware-vmafd/bin/vecs-cli entry list --store vsphere-webclient
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --text --store vsphere-webclient --alias vsphere-webclientGenerate
/usr/lib/vmware-vmca/bin/certool --genkey --privkey=/storage/certmanager/vpxd.priv --pubkey=/storage/certmanager/vpxd.pub --server=localhost
/usr/lib/vmware-vmca/bin/certool --server=localhost --gencert --privkey=/storage/certmanager/vpxd.priv --cert=/storage/certmanager/vpxd.crt --config=/var/tmp/vmware/vpxd.cfg
/usr/lib/vmware-vmafd/bin/vmafd-cli get-machine-id --server-name localhost
/usr/lib/vmware-vmafd/bin/dir-cli service list --login [email protected] --password *****
/usr/lib/vmware-vmafd/bin/dir-cli service update --cert /storage/certmanager/vpxd.crt --name vpxd-6368669f-591a-44fa-bfb3-a76b166bfed6 --login [email protected] --password *****
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --text --store vpxd --alias vpxd
/usr/lib/vmware-vmafd/bin/vecs-cli entry delete -y --store vpxd --alias vpxd
/usr/lib/vmware-vmafd/bin/vecs-cli entry list --store vpxd
/usr/lib/vmware-vmafd/bin/vecs-cli entry create --store vpxd --alias vpxd --cert /storage/certmanager/vpxd.crt --key /storage/certmanager/vpxd.priv
/usr/lib/vmware-vmafd/bin/vecs-cli entry list --store vpxd
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --text --store vpxd --alias vpxdGenerate vpxd-extension certificate
/usr/lib/vmware-vmca/bin/certool --genkey --privkey=/storage/certmanager/vpxd-extension.priv --pubkey=/storage/certmanager/vpxd-extension.pub --server=localhost
/usr/lib/vmware-vmca/bin/certool --server=localhost --gencert --privkey=/storage/certmanager/vpxd-extension.priv --cert=/storage/certmanager/vpxd-extension.crt --config=/var/tmp/vmware/vpxd-extension.cfg
/usr/lib/vmware-vmafd/bin/vmafd-cli get-machine-id --server-name localhost
/usr/lib/vmware-vmafd/bin/dir-cli service list --login [email protected] --password *****
/usr/lib/vmware-vmafd/bin/dir-cli service update --cert /storage/certmanager/vpxd-extension.crt --name vpxd-extension-6368669f-591a-44fa-bfb3-a76b166bfed6 --login [email protected] --password *****
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --text --store vpxd-extension --alias vpxd-extension
/usr/lib/vmware-vmafd/bin/vecs-cli entry delete -y --store vpxd-extension --alias vpxd-extension
/usr/lib/vmware-vmafd/bin/vecs-cli entry list --store vpxd-extension
/usr/lib/vmware-vmafd/bin/vecs-cli entry create --store vpxd-extension --alias vpxd-extension --cert /storage/certmanager/vpxd-extension.crt --key /storage/certmanager/vpxd-extension.priv
Update EAM and
/usr/bin/python /usr/lib/vmware-vpx/scripts/updateExtensionCertInVC.py -e com.vmware.vim.eam -s is-dhcp36-107.isl.vmware.com -c /storage/certmanager/vpxd-extension.crt -k /storage/certmanager/vpxd-extension.priv - [email protected] -p *****
/usr/bin/python /usr/lib/vmware-vpx/scripts/updateExtensionCertInVC.py -e com.vmware.rbd -s is-dhcp36-107.isl.vmware.com -c /storage/certmanager/vpxd-extension.crt -k /storage/certmanager/vpxd-extension.priv - [email protected] -p *****
/usr/lib/vmware-vmafd/bin/vecs-cli entry list --store vpxd-extension
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --text --store vpxd-extension --alias vpxd-extension
service-control --stop --ignore --all
service-control --start --allon Certain occations when the vCenter is upgraded, Plugins like pure, Netapp, NSX, SRM etc can cause incompatibility and prevent the webclient from loading up/Malfunctioning
Starting vSphere 6.7, we have a config file to white list and black list plugins which helps us to flag specific Malicious/incompatible plugins which prevents the web client form loading up
the symptoms to this include
* web client hangs at a blue, loading screen.
* web client loads but does not display any inventory object
* web client does not allow to click on the inventory objects (home button and task and events are sometimes clickable)
The quickest way to sort out these specious plugin is by adding the plugin id to blacklist to the respective UI/flex file comparability config.
UI(html5):
/etc/vmware/vsphere-ui/compatibility-matrix.xml
root@is-dhcp36-107 [ /etc/vmware/vsphere-ui ]# cat compatibility-matrix.xml
<!--
This file lets you define a WHITE LIST and a BLACK LIST of plugins to control your own setup.
It overrides the internal black and white lists that are hard-coded in this release.
Fling Note: until further notice all plugins are disabled by the HTML5 client except SDK samples.
Use this file to re-enable specific HTML plugins during your testing.
-->
<Matrix>
<pluginsCompatibility>
<!--
WHITE LIST:
Add this to enable all plugins whose plugin-package id is com.acme.example.myplugin:
<PluginPackage id="com.acme.myplugin" status="compatible"/>
Or this to specify all versions greater or equal to 2.1.0:
<PluginPackage id="com.acme.myplugin" version=[2.1.0,] status="compatible"/>
Or this to enable all plugins starting with com.acme:
<PluginPackage id="com.acme.*" status="compatible"/>
-->
<!--
BLACK LIST:
Add this to disable a plugin whose plugin-package id is com.acme.example.myplugin:
<PluginPackage id="com.acme.myplugin" status="incompatible"/>
-->
</pluginsCompatibility>
</Matrix>
vsphere-client (flex)
/etc/vmware/vsphere-client/compatibility-matrix.xml
root@is-dhcp36-107 [ /etc/vmware/vsphere-client ]# cat compatibility-matrix.xml
<!--
The 'id' value allows for standard java regular expressions. The actual plugin id
is matched against this regular expression.
The 'version' values must be a string in any of the following formats. If skipped
it indicates any version.
Version: An exact version, e.g. 6.0.0, 5.5, etc. The format allows for maximum
of 4 dotted numbers.
Interval: (, 6.4], [6.5, 7.0), (7.5, ). Use empty strings to mark infinity values.
Range: Several versions and intervals can be mixed in one single string
producing a set of value, e.g. ( ,6.4), 6.8.3, 6.9.1, [7.5.2.2, ).
Each item in the set is separated from the others using comma ",".
Each item in the set can be either version or interval.
The 'status' can be any of the following strings: unknown,
incompatible, compatible, certified
-->
<Matrix>
<pluginsCompatibility>
<!--
'Incompatible' plugins are not loaded. You can use this to 'blacklist'
plugins if needed. To prevent specific plugin package(s) from
loading, use the template entry below as guidance how to add new records
with the actual id and version of the plugin you want to prevent from loading.
The plugin ids can be taken from the plugin-package.xml file of each plugin.
A few well known set of plugins locations (on the vCenter Appliance):
/usr/lib/vmware-vsphere-client/plugin-packages/
/etc/vmware/vsphere-client/vc-packages
/etc/vmware/vsphere-client/cm-service-packages
On Windows the following locations can be checked:
<INSTALL DRIVE>\ProgramData\vCenterServer\runtime\vsphere-client\plugin-packages
<INSTALL DRIVE>\ProgramData\vCenterServer\cfg\vsphere-client\vc-packages
<INSTALL DRIVE>\ProgramData\vCenterServer\cfg\vsphere-client\cm-service-packages
-->
<!--
<PluginPackage id="com.foo.plugin.id" version="1.0.0" status="incompatible"/>
<PluginPackage id="net.bar.plugin.id" version="(,2.1]" status="incompatible"/>
-->
<!--
The sample section below shows 'whitelist' definition. Compatible plugins
are loaded. All others are declared as incompatible (due to the id regex),
thus effectively forbidding them.
The approach limits the list of plugins loaded only to a small 'white' list.
This allows for vsphere-client to work in a 'safe-like' mode.
Below are predefined sets of plugins for your convenience:
1st-party, core:
com.vmware.vsphere.client,
com.vmware.ds,
com.vmware.ssoadminui,
com.vmware.vsphere.client.modules,
com.vmware.license.client,
com.vmware.opsmgmt.client
1st-party extended (in addition to the above):
com.vmware.loganalyzer,
com.vmware.vsphere.client.telemetry
2nd-party (basically anything that comes already pre-bundled with the
vCenter Appliance and is not in the above two sets):
com.vmware.vca.marketing.ngc.ui,
com.vmware.vco
-->
<!--
<PluginPackage id="com.vmware.vsphere.(client|ds|ssoadminui|client.modules)" status="compatible"/>
<PluginPackage id="com.vmware.license.client" status="compatible"/>
<PluginPackage id="com.vmware.opsmgmt.client" status="compatible"/>
<PluginPackage id=".*" status="incompatible"/>
-->
</pluginsCompatibility>
</Matrix>The plugin ID can be found on the extension manager under vCenter MOB. https://vc-fqdn/mob